If we want to be clever, we can reopen stderr by, prior to dup2 ing the memory fd to stderr, we choose another fd to dup stderr to, and then in the shellcode, we dup2 that other fd back to stderr. But I don't know. The Source-Code of Mempodipper: Mempodipper is an exploit for CVE I determined another way to do this, using ptrace. 
| Uploader: | Gugis |
| Date Added: | 23 May 2014 |
| File Size: | 50.92 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 32836 |
| Price: | Free* [*Free Regsitration Required] |
All Rights Reverse Engineered. Where do we write to?
For SUID programs, ptracing will drop its privileges, but that's fine, since we simply want to find internal memory locations. If you're a student trying to learn about things or have otherwise legitimate reasons, we can talk.
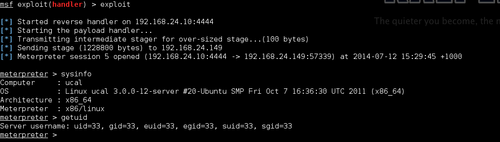
Let's take a look at the write function:. Introducing Mempodipperan exploit for CVE Notify me of new posts via email. I've created a standalone utility that returns the offset, as well as integrating it into the main mempodipper source.
Extract from the Official Blog: Gentoo is smart enough to remove read permissions on SUID binaries, making it impossible to find the exit plt offset using objdump. So we've chosen su wisely. So finally, we pass our opened fd from the child process back to the parent process using some very black unix domain sockets magicdo our dup2 ing, and exec into su with the shell code.
You are commenting using your WordPress.
It turns out, of course, that the permissions checking was done poorly. Mempodipper is an exploit for CVE Anyone with the correct permissions could write to process memory. Maybe you think you can trick fxploit ptrace code? You are commenting using your Google account. There is one remaining objection. Now naturally, we want to write into the memory of suid processessince then we can get root. We fork a child, and inside of that child, we exec to a new process.
I essential for this webpage publish admin truly thanks i will glimpse your future sharings jempodipper bookmarked your webpage. Let's do the first one first and second one second. Take a look at this:.
ampbkama.tk
You are commenting using your Twitter account. Leave a Reply Cancel reply Enter your comment here Here's how to get around it.
Wordpress might sometimes add ADs. I observed what i was searching for right here. I wrote the shellcode for bit and bit by hand.
Mempodipper: Gain Root without Local Root Kernel Exploits | G.N.A. Team
Follow us on Twiiter: So to find the right place to write to, let's check out the assembly surrounding the printing of explot "Unknown id: The code to do this is in the "fedora" branch of the git repository, and a video demonstration is also available. Expllit determined another way to do this, using ptrace. So naturally, we want to write to 0x minus the number of letters in the string "Unknown id: We can, in an exploit, automate the finding of the exit plt symbol with a simple bash one-liner:.

Комментариев нет:
Отправить комментарий